Configure Single Sign-On
Follow the steps below to configure single sign-on for AWS Identity Center.Go to the Unblocked SSO Settings
Navigate to the Settings section of the Unblocked web app.
Under Team Settings, select Security.
Locate the Single Sign-On section and click Configure.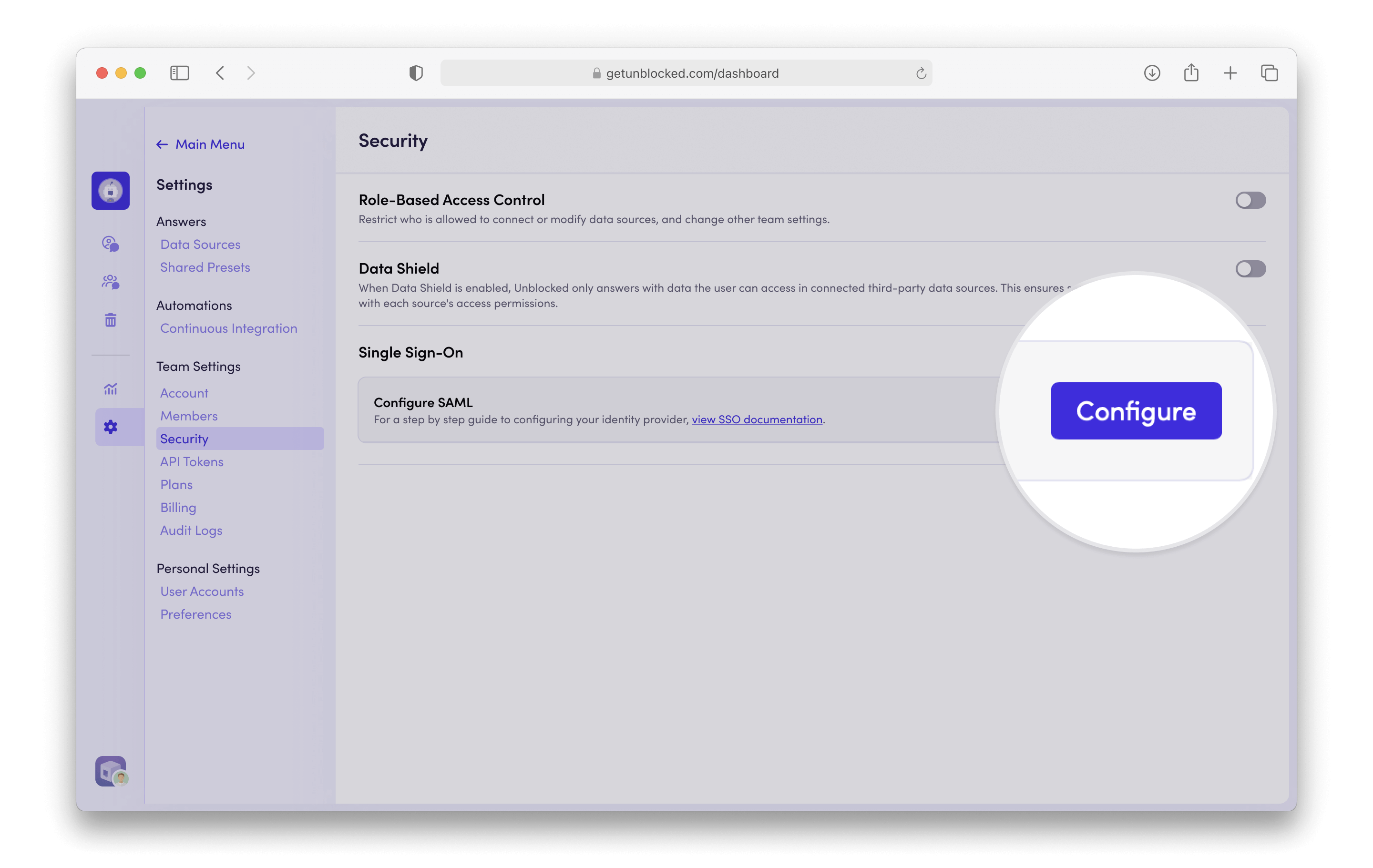

Create an AWS Identity Center application
From IAM Identity Center, navigate to the Applications tab, and click Add application.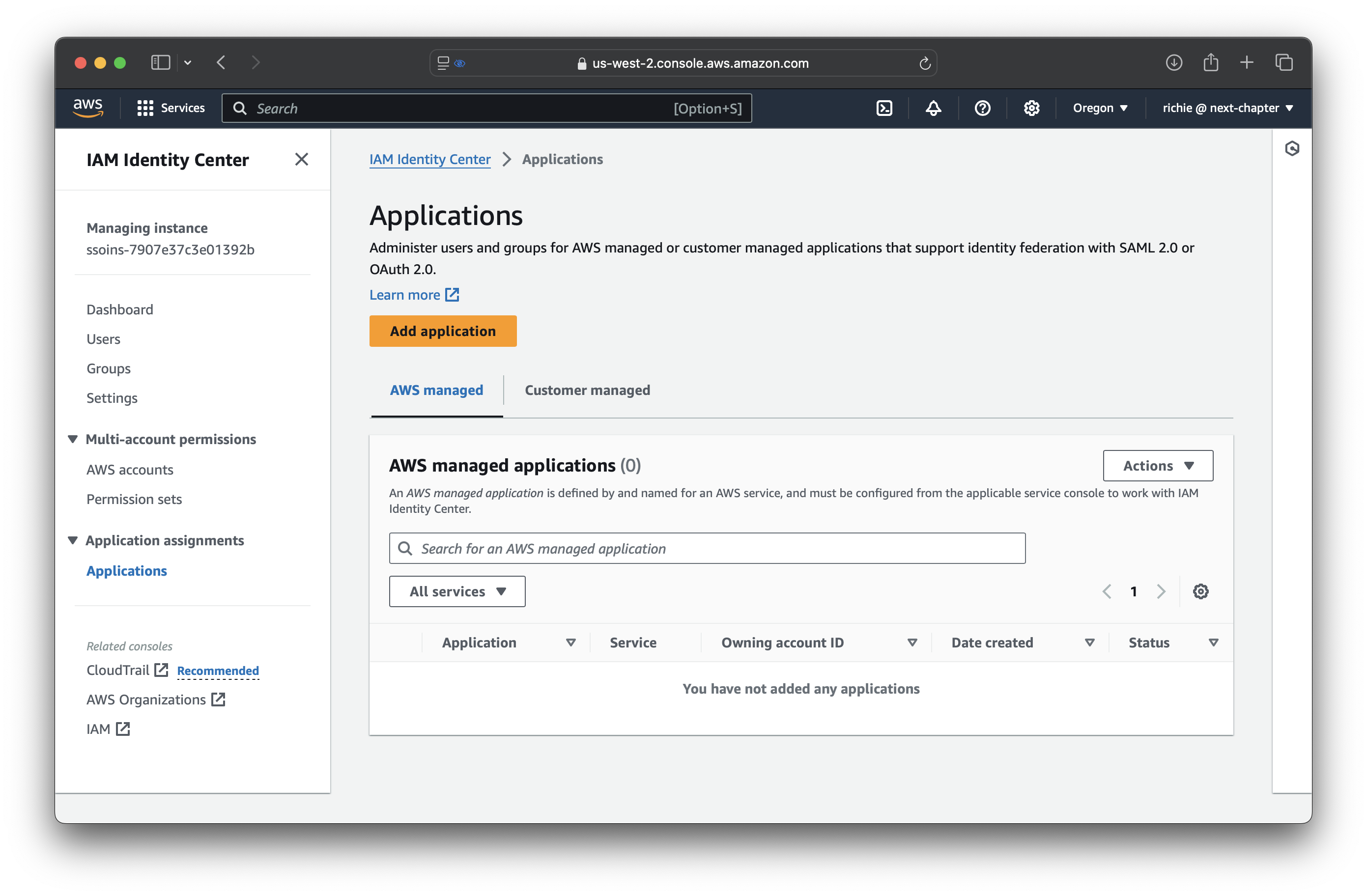
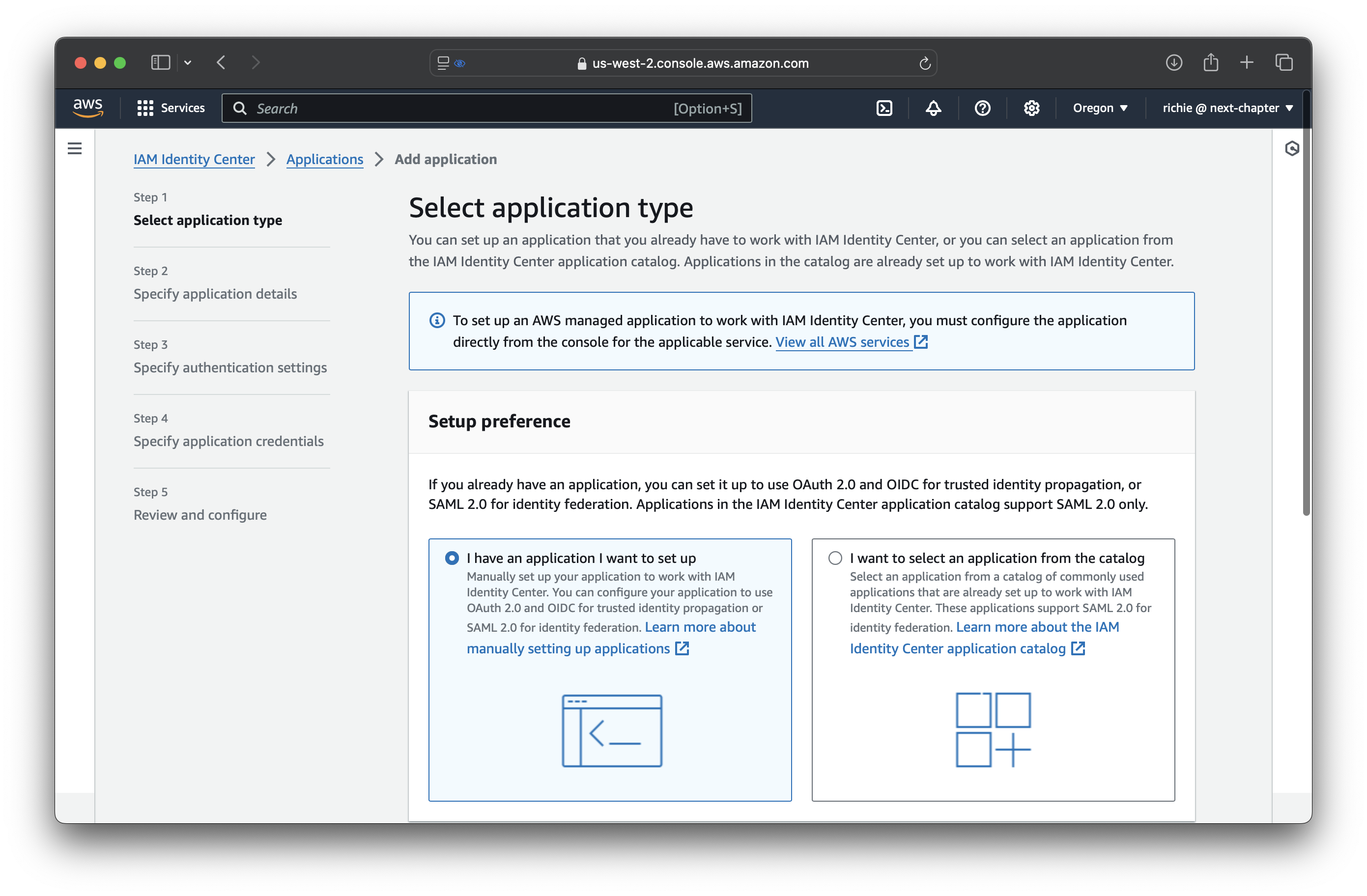
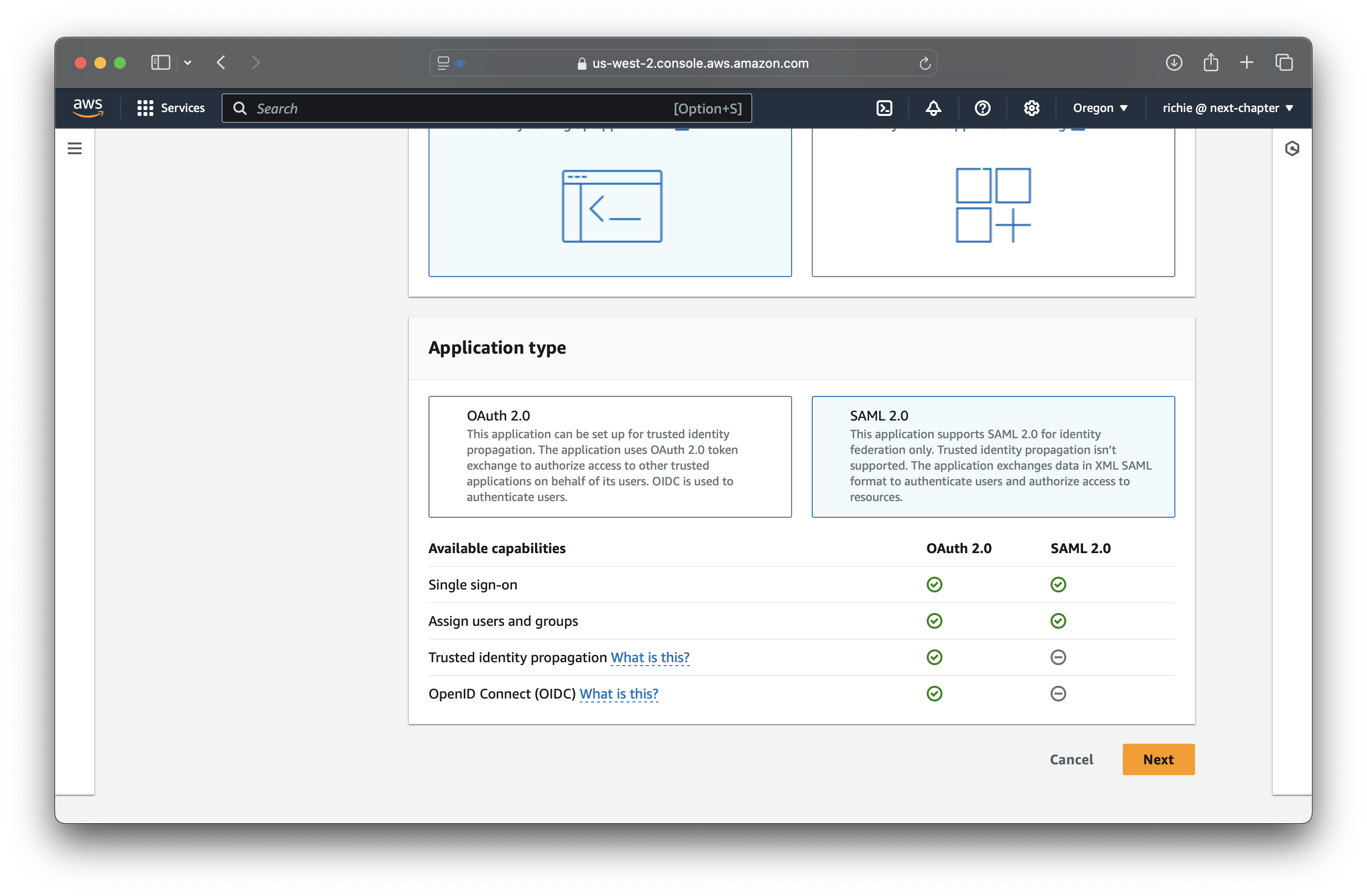
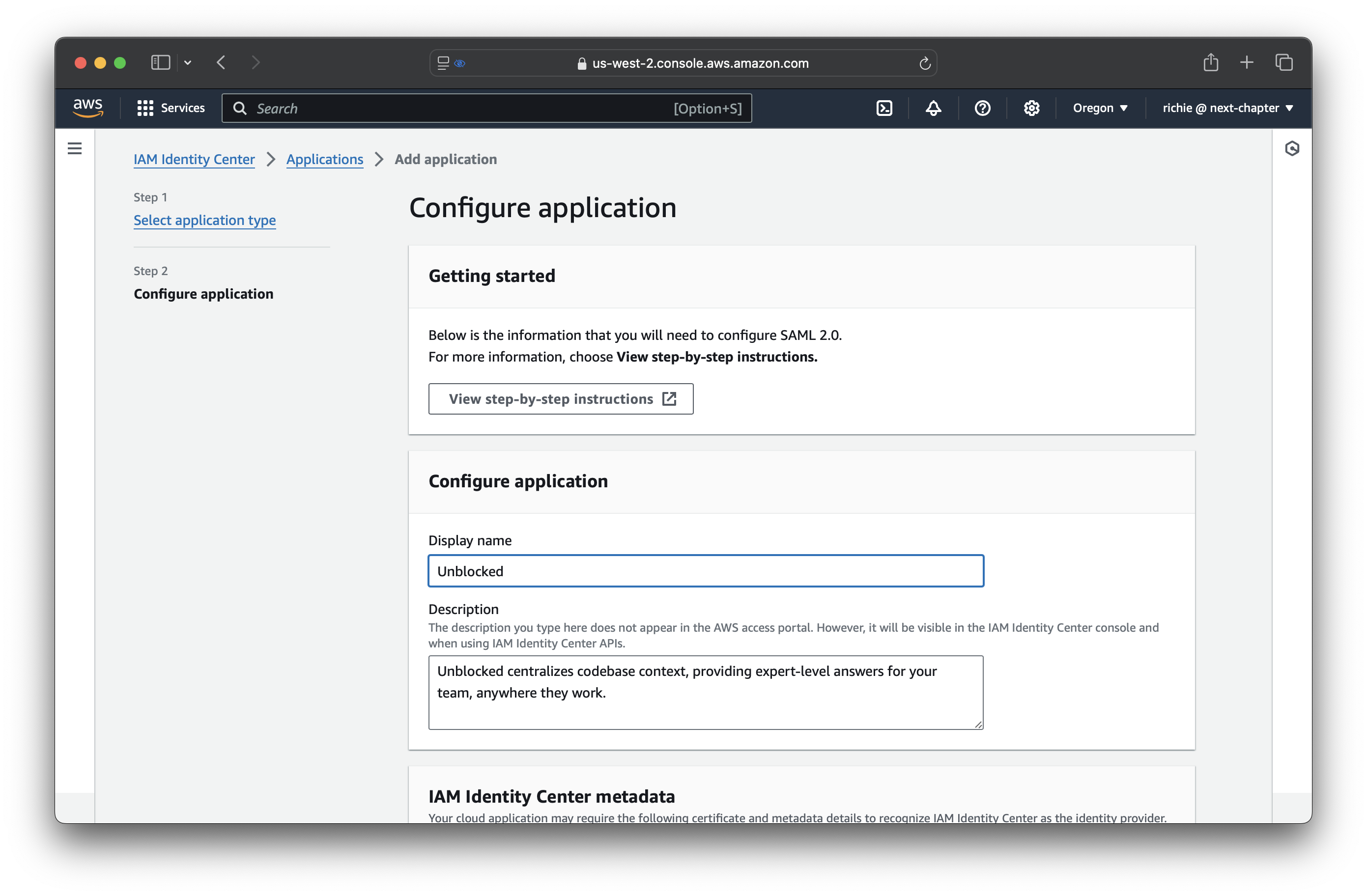




Configure IAM Identity Center metadata
Copy the following information from the IAM Identity Center metadata section
and paste it into Unblocked.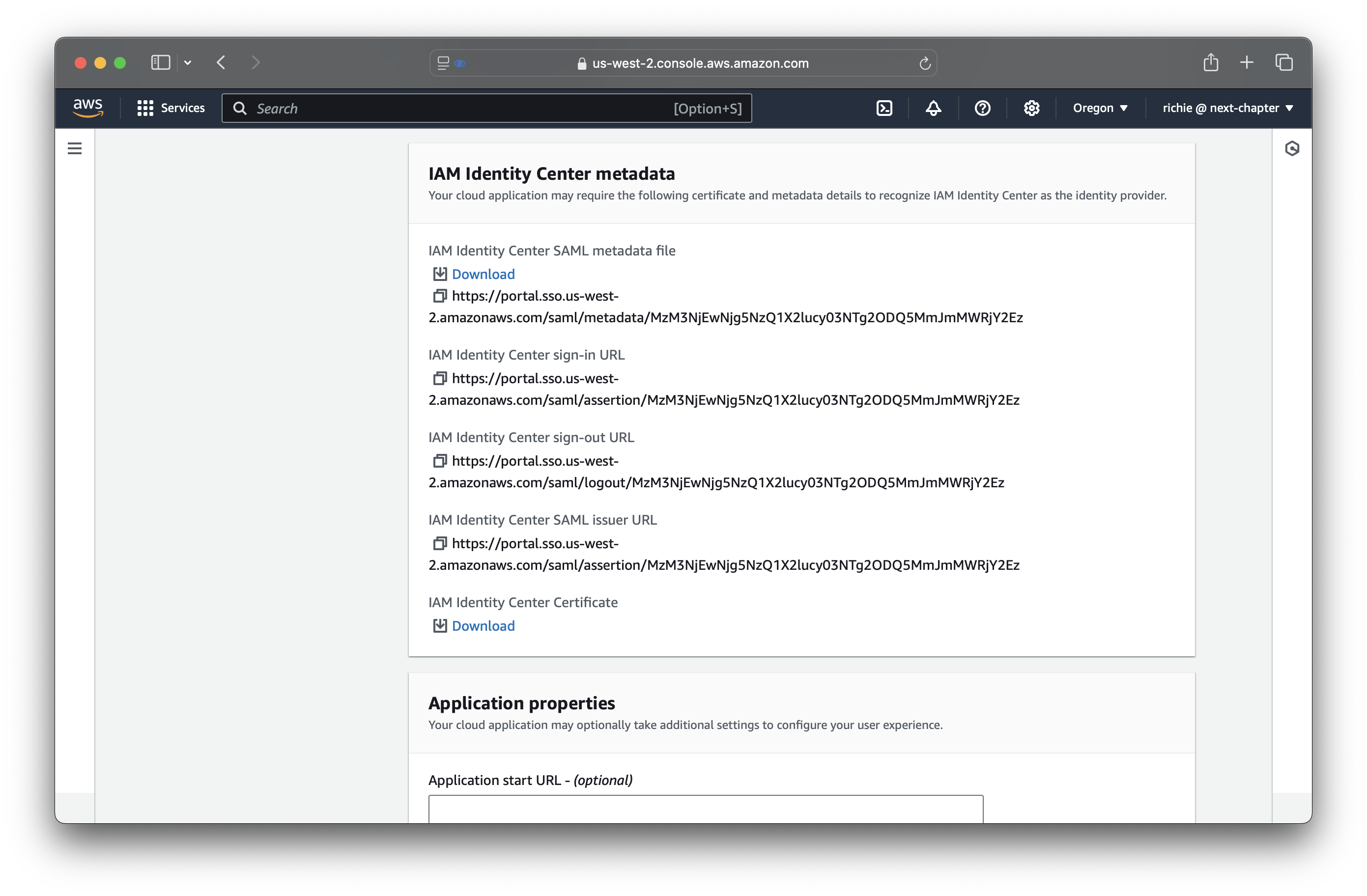
- IAM Identity Center sign-in URL
- IAM Identity Center SAML issuer URL
- IAM Identity Center Certificate

Configure Application metadata
Copy the following values from Unblocked into the Application metadata section in AWS identity center:
- Application ACS URL
- Application SAML audience
Configure attribute mappings
From the Actions menu, select Edit attribute mappings.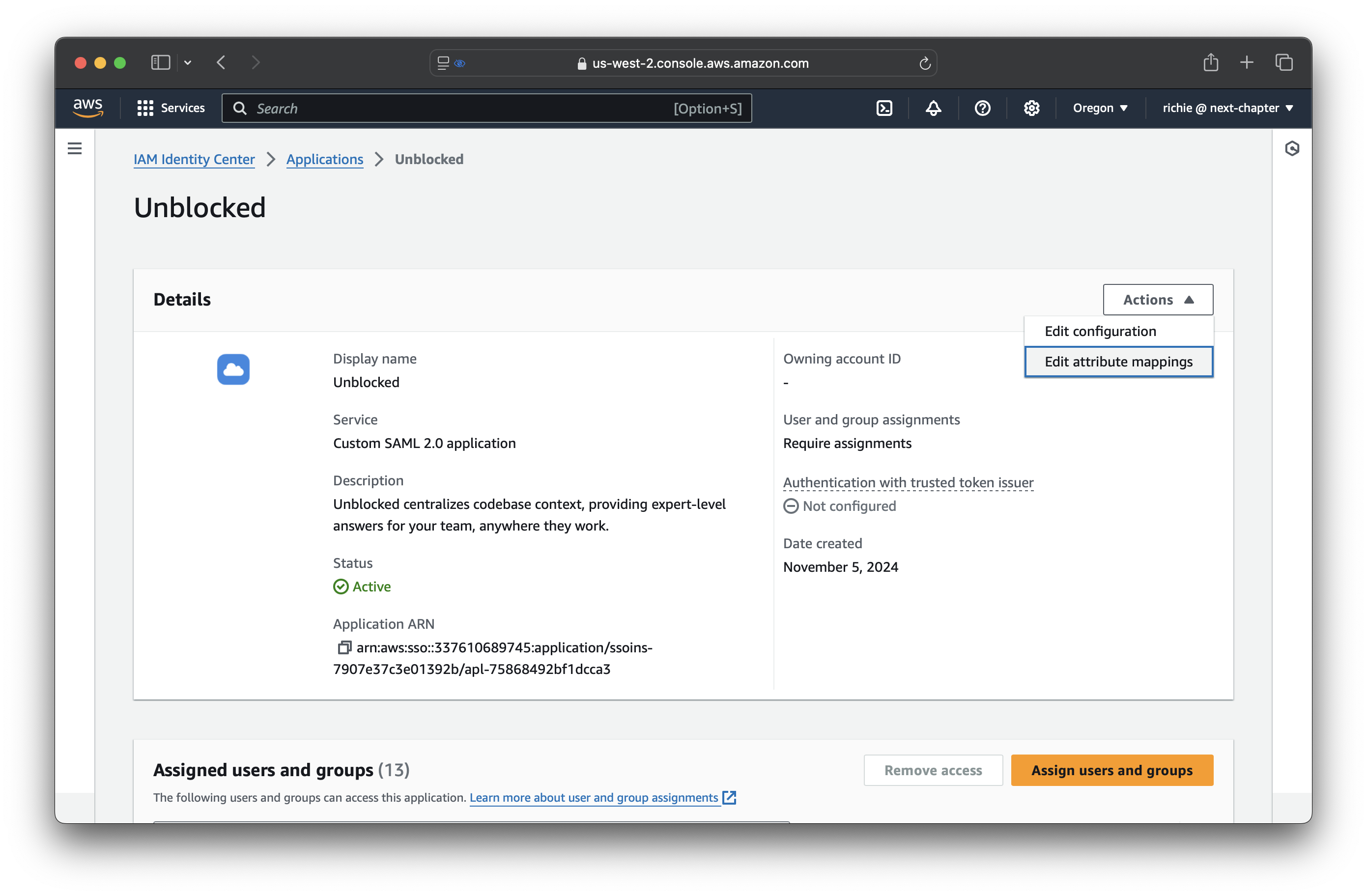
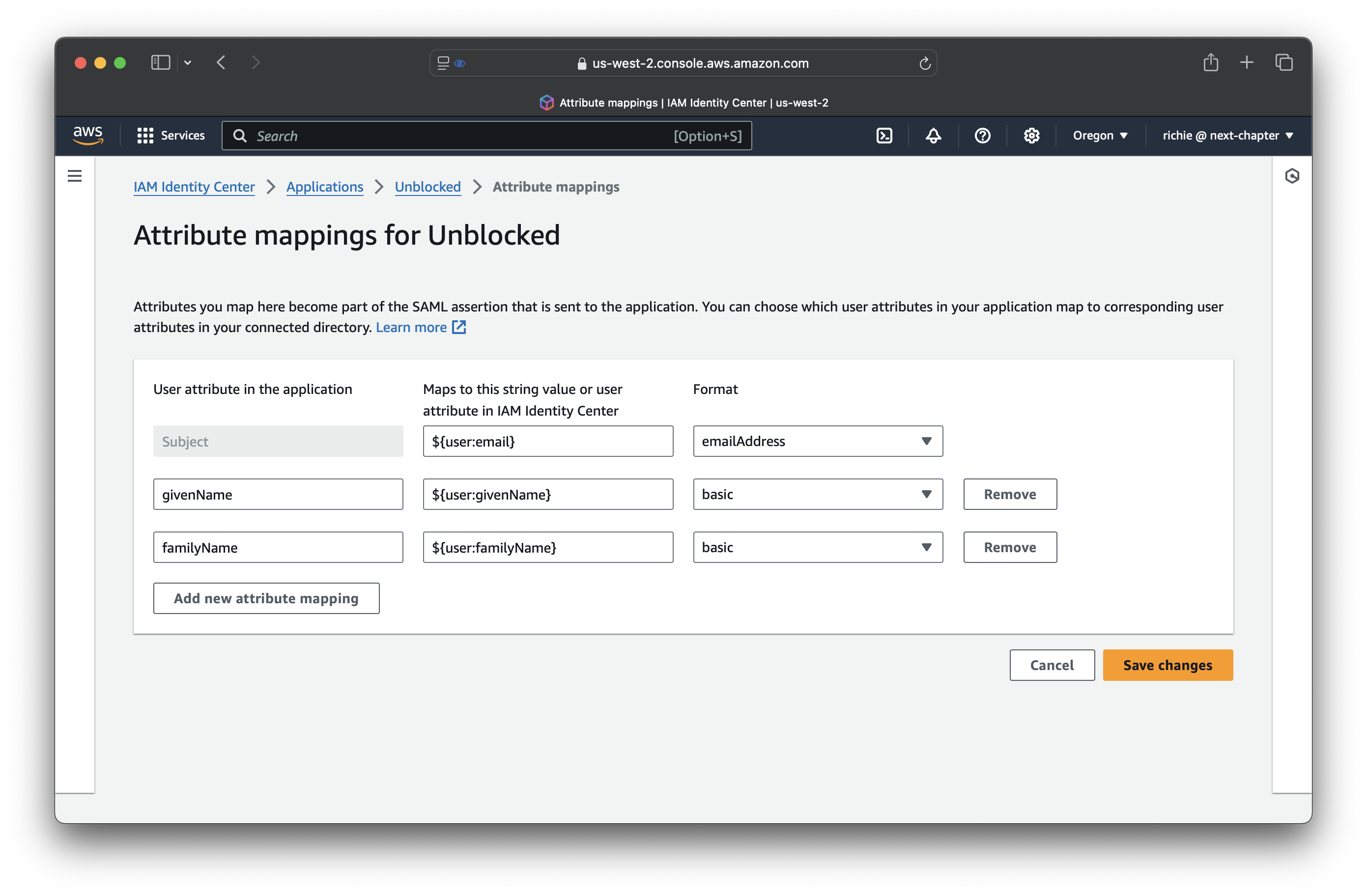

| User attribute in Unblocked | User attribute in Identity Center | Format |
|---|---|---|
Subject | ${user.email} | emailAddress |
givenName | ${user.givenName} | basic |
familyName | ${user.familyName} | basic |

Enforce SSO
Once SSO is configured, you can enforce its use for your team. This means all team members will be required to sign in using your SSO provider. There are two enforcement options:- SSO Only: Users will be required to sign in to Unblocked using SSO. You may need to sign in with SSO before enabling this option.
- SSO, a Source Code System, or Slack: Users can sign in using either SSO, their source code system (e.g., GitHub, Bitbucket, or GitLab), or Slack.
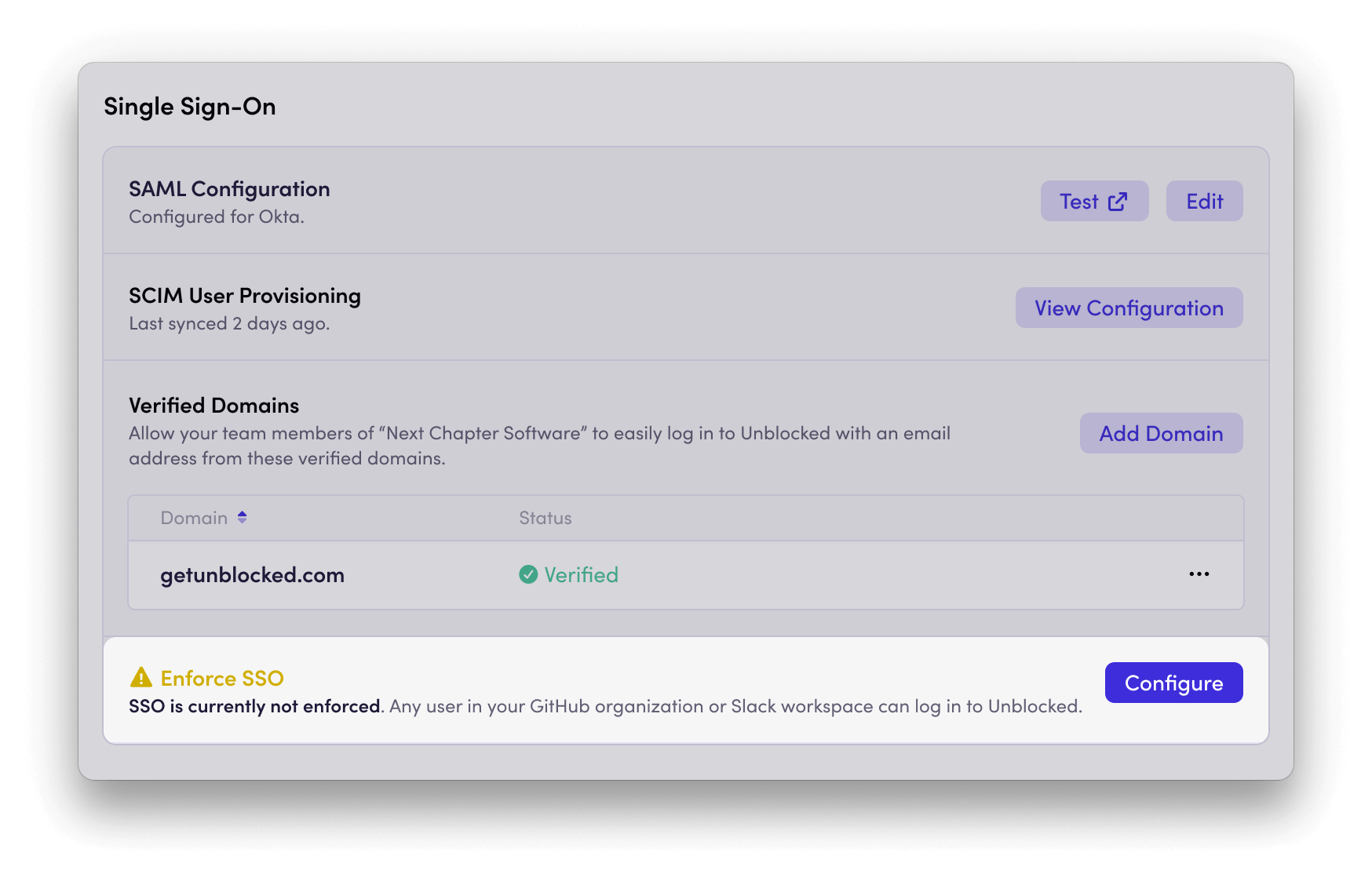
Allowed Email Domains
Verifying a domain ensures that users who enter an email address from that domain on the Unblocked sign-in page are automatically directed to your SSO login. This creates a seamless login experience and routes users through the correct authentication flow. You can add multiple domains to enable SSO login detection for users with different email addresses. To verify a domain:
Once the domain is verified, any user who enters an email address matching that domain on the Unblocked sign-in page will see the SSO login option for your SAML provider.
Verifying a domain only controls the visibility of the SSO login option and does not automatically grant access to
your Unblocked team. Access to Unblocked is still managed through user and group assignments in your identity provider (IdP).
Download Unblocked Logo
To help your users easily recognize Unblocked in their identity provider dashboard, download the Unblocked logo for use in your SSO application.